
pico CTF Reverse Engineering
March 2, 2023 CTF
Transformation
The transformation was recognized by the Magic option in CyberChef and is Encode_text('UTF-16BE (1201)').
The flag is picoCTF{16_bits_inst34d_of_8_75d4898b} .
keygenme-py
The first and last part of the flag are defined in the variables
key_part_static1_trial = "picoCTF{1n_7h3_|<3y_of_"
key_part_static2_trial = "}"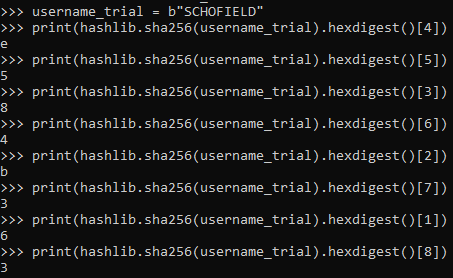
The middle part is dynamicaly created and can be reversed from the function check_key. If we take the binary representation ot the username_trail and run the second part of each if statment we get the full synamic flag part.
The flag is picoCTF{1n7h3|<3y_of_e584b363} .
crackme-py
We have a variable called bezos_cc_secret at the top of the file and a deode function that uses ROT 47. The flag picoCTF{1|\/|_4_p34||ut_502b984b} can be decoded with CyberChef.
vault-door-training
If we open up the Java file in a editor we can see that the flag is written in plaintext in the passwordcheck.
public boolean checkPassword(String password) {
return password.equals("w4rm1ng_Up_w1tH_jAv4_be8d9806f18");
}The flag is picoCTF{w4rm1ng_Up_w1tH_jAv4_be8d9806f18} .
vault-door-1
If we open the Java file in an editor we can see that each character if the password is checked in a function. If we put the comparasinses in the correct order we get the password.
password.charAt(0) == 'd' &&
password.charAt(1) == '3' &&
password.charAt(2) == '5' &&
password.charAt(3) == 'c' &&
password.charAt(4) == 'r' &&
password.charAt(5) == '4' &&
password.charAt(6) == 'm' &&
password.charAt(7) == 'b' &&
password.charAt(8) == 'l' &&
password.charAt(9) == '3' &&
password.charAt(10) == '_' &&
password.charAt(11) == 't' &&
password.charAt(12) == 'H' &&
password.charAt(13) == '3' &&
password.charAt(14) == '_' &&
password.charAt(15) == 'c' &&
password.charAt(16) == 'H' &&
password.charAt(17) == '4' &&
password.charAt(18) == 'r' &&
password.charAt(19) == '4' &&
password.charAt(20) == 'c' &&
password.charAt(21) == 'T' &&
password.charAt(22) == '3' &&
password.charAt(23) == 'r' &&
password.charAt(24) == '5' &&
password.charAt(25) == '_' &&
password.charAt(26) == '7' &&
password.charAt(27) == '5' &&
password.charAt(28) == '0' &&
password.charAt(29) == '9' &&
password.charAt(30) == '2' &&
password.charAt(31) == 'e';The flag is picoCTF{d35cr4mbl3_tH3_cH4r4cT3r5_75092e} .
file-run1
If we open up the file in Ghidra and go the the main function we can see that the flag is printed out.
The flag is picoCTF{U51N6_Y0Ur_F1r57_F113_e5559d46} .