
HTB Crypto Challenges
March 27, 2021 HackTheBox
TwoForOne
Alice sent two times the same message to Bob.
We throw the two .pem files in Crypto Playground and get two RSA public keys with the same modulo. The encryption is vulnerable to a common modulus attack:
from base64 import b64decode, b64encode
from libnum import xgcd, invmod, n2s
e1 = int('', 16)
e2 = int('', 16)
N = int('', 16)
c1 = ''
c2 = ''
c1 = int.from_bytes(b64decode(c1), 'big')
c2 = int.from_bytes(b64decode(c2), 'big')
def common_modulus(e1, e2, c1, c2, N):
# Extended Euclidean algorithm
a, b, d = xgcd(e1,e2)
# Invert negative factor
if b < 0:
c2 = invmod(c2, N)
b = -b
if a < 0:
c1 = invmod(c1, N)
a = -a
# Get the message (c1^a * c2^b) % N
m = (pow(c1,a,N) * pow(c2,b,N)) % N
return [m, a, b, d]
m, _, _, _ = common_modulus(e1,e2,c1,c2,N)
flag = n2s(m)
print(flag)
xorxorxor
Who needs AES when you have XOR?
We get a program that XORs a key with the flag and the resulting cipher is found in the output.txt. The first 4 characters "134af6e1" are know to be "HTB{" so we can use CyberChef and the XOR Brute Force function to calculate the key which is "5b1eb49a".
Flippin-Bank
The Bank of the World is under attack. Hackers found a way in and locked the admins out. However, the netcat authentication by the intruders is not perfectly secure. Could you help the admins log in?
First we obtain the ciphertext of username cdmin and password g0ld3n_b0y. The first block (i.e. the first 16 bytes) of this ciphertext is the ciphertext of logged_username=, the ciphertext of this block is also the IV for our second block (CBC Mode). In decryption mode the IV is XORed with the result of the decryption function, we can thus modify bits in the second block by flipping the corresponding bit in the IV.
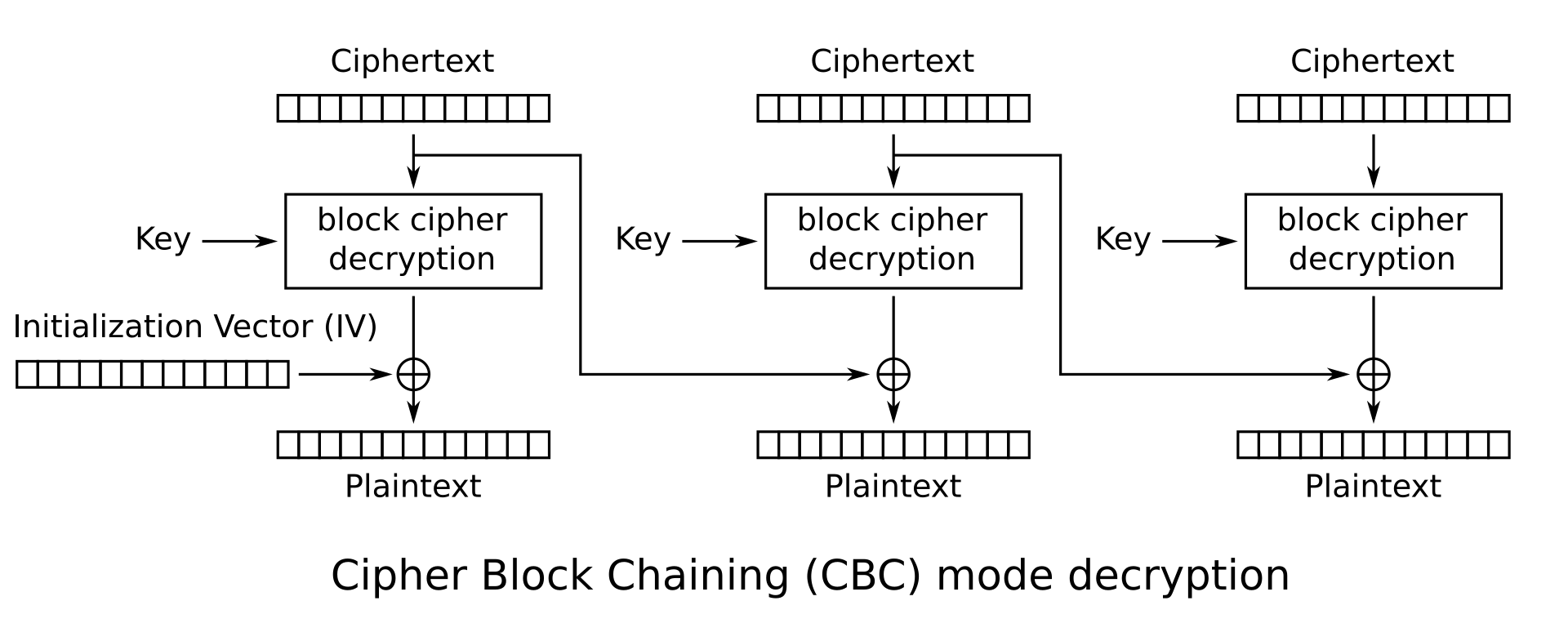
The binary representation of a is 1100001, the binary representation of c is 1100011. We thus need to flip the second bit of the first byte of the ciphertext giving as a modified ciphertext which when fed into the program decrypts to <16 random bytes>admin&password=g0ld3n_b0y giving us the flag.
Or you can automate this task using any character instead of a, e.g. b:
k = 'cipher from bdmin + g0ld3n_b0y'
from binascii import unhexlify, hexlify
c = unhexlify(k)
cc = ord('a') ^ ord('b')
ccc = hexlify(bytearray([c[0] ^ cc]) + c[1:])
print(ccc)