
Hack me. If you can!
March 23, 2021 CTF
Hack me. If you can! is a hacking challenge created by the University of Applied Sciences in Augsburg.
Can you break me? - Here is the file that Pepper sent to Salt. Help Salt figure out what's inside!
We can guess that the first line in the text file "YAMK EAAMKWA BXZAF UFB MAKKAF," reads "Sehr geehrte Damen und Herren" and that "MYX_OFFJY" is the beginning of the flag "HSA_INNOS". From there we can gradually exchange every letter with the corresponding encrypted letter. I wrote a little python script to automate the process of decrypting the text.
cipher = ['a', 'b', 'c', 'd', 'e', 'f', 'g', 'h', 'i', 'j', 'k', 'l', 'm', 'n', 'o', 'p', 'q', 'r', 's', 't', 'u', 'v', 'w', 'x', 'y', 'z']
corresp =['e', 'd', 'f', 'b', 'g', 'n', 'x', 'c', 'w', 'o', 'r', 'p', 'h', 'n', 'i', 'q', 'k', 'r', 'v', 'l', 'u', 'v', 't', 'a', 's', 'm']
enflag = 'MYX_OFFJY_CTXE_PUOHQDKJIFCJG'.lower()
deflag = ''
for i in range(len(enflag)):
if enflag[i] == '_':
deflag += '_'
continue
elif enflag[i] == ' ':
deflag += ' '
continue
for j in range(len(cipher)):
if enflag[i] == cipher[j]:
deflag += corresp[j]
print(deflag)FLAG: hsa_innos_flag_quickbrownfox
Who am I? - Here is the original file. What's it all about?
We get a PDF file that states, 'I am not what you think I am. Who am I?'. The command foremost -v Challenge.pdf extracts a file called flag.txt containing the flag.
FLAG: HSA_INNOS_FLAG_5KIOH60XCVP832JN
Are you joking me? - Help Salt one more time and find the flag!
We get a GO program that prints 'Go This Way! Find my Secret.' when executed. A simple strings challenge | grep HSA gives us the flag.
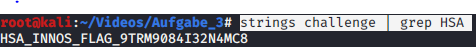
FLAG: HSA_INNOS_FLAG_9TRM9084I32N4MC8
Are you joking me? - You are in demand again! Please help Salt.
We are provided with a challenge.wav file that provides a hint when opened with Sonic Visualizer as a Spectrogram. When the same WAV file is examined in Robot36 – SSTV Image Decoder the flag is displayed.


FLAG: HSA_innos_NLBR89BGKLMOET8334
Can you capture the flag? - Take a look at the network recording with a suitable tool and find the flag.
We are provided a capture_easy.pcapng, upon inspection with Wireshark we can see numerous request with different URLs. strings capture_easy.pcapng | grep Host visualizes ASCII art. There is a message encoded in the first character of each line. We can use the following bash script to retrieve it:
strings capture_easy.pcapng | grep Host | awk '{print $2;}' | tr -d '\n'
FLAG: HSA_INNOS_FLAG_0HDP71IL58T1
Don't care? Ransomware! - Can you help Salt get its data?
We get an info file containing the obfuscated strings
AES-CTR, KEY
e1e60272534605d4e6f01ab3b40f4c93b663cb0d08c979491fac3fb662505e91, 386c5159b1d283698e39a56c138dfabd.txt, OpenSSL_enc-dand IV 54b8fb54458e2ade1649e78848200f24. Combined into the following command
openssl enc -aes-256-ctr -d -iv 54b8fb54458e2ade1649e78848200f24 -K e1e60272534605d4e6f01ab3b40f4c93b663cb0d08c979491fac3fb662505e91 -in 386c5159b1d283698e39a56c138dfabd.enc -out 386c5159b1d283698e39a56c138dfabd.txtwe can decrypt the message.
FLAG: HSA_INNOS_FLAG_17AB6923CDBDD4CE
Combine & Conquer - Salt is close to the goal, he needs support. Find the flag!
We get two text files containing base64, after converting it from base64 this simple xor python script displays the flag.
import base64
a = '3d91d7f4e9844f2b03dbf4c0dca4f9281ddd03abe2844f2b03dbd4c0dca40102'
b = '75c296bda7ca00785c9db8819bfbc81a2ee43793d7b4761932eee0f9eb963635'
a = bytearray.fromhex(a)
b = bytearray.fromhex(b)
def xorArray(x,y):
r = []
for i in range(32):
r.append(x[i] ^ y[i])
return bytearray(r)
print(xorArray(a,b))FLAG: HSAINNOS_FLAG_123948509215497277
Crack me! - Help Salt one last time to get the flag.
We get a password protected ZIP-File called important.zip. With fcrackzip -u -D -p rockyou.txt important.zip the password is found within seconds.
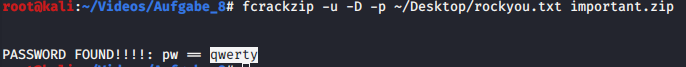
FLAG: HSA_INNOS_FLAG_6N84TG5PADMC52LL