
Google CTF Beginners Quest 2021
October 22, 2022 CTF
Google CTF Beginners Quest is a set of beginner challenges created to provide a good introduction to the world of CTFs.
Vienna - Chemical plant
Challenge: CCTV (rev) You arrive at your destination. The weather isn't great, so you figure there's no reason to stay outside and you make your way to one of the buildings. No one bothered you so far, so you decide to play it bold - you make yourself a cup of coffee in the social area like you totally belong here and proceed to find an empty room with a desk and a chair. You pull out our laptop, hook it up to the ethernet socket in the wall, and quickly find an internal CCTV panel - that's a way better way to look around unnoticed. Only problem is... it wants a password.
We are provided a link to the mentioned CCTV, which is password protected. The website's source code shows us how the algorithm used to validate the password works.
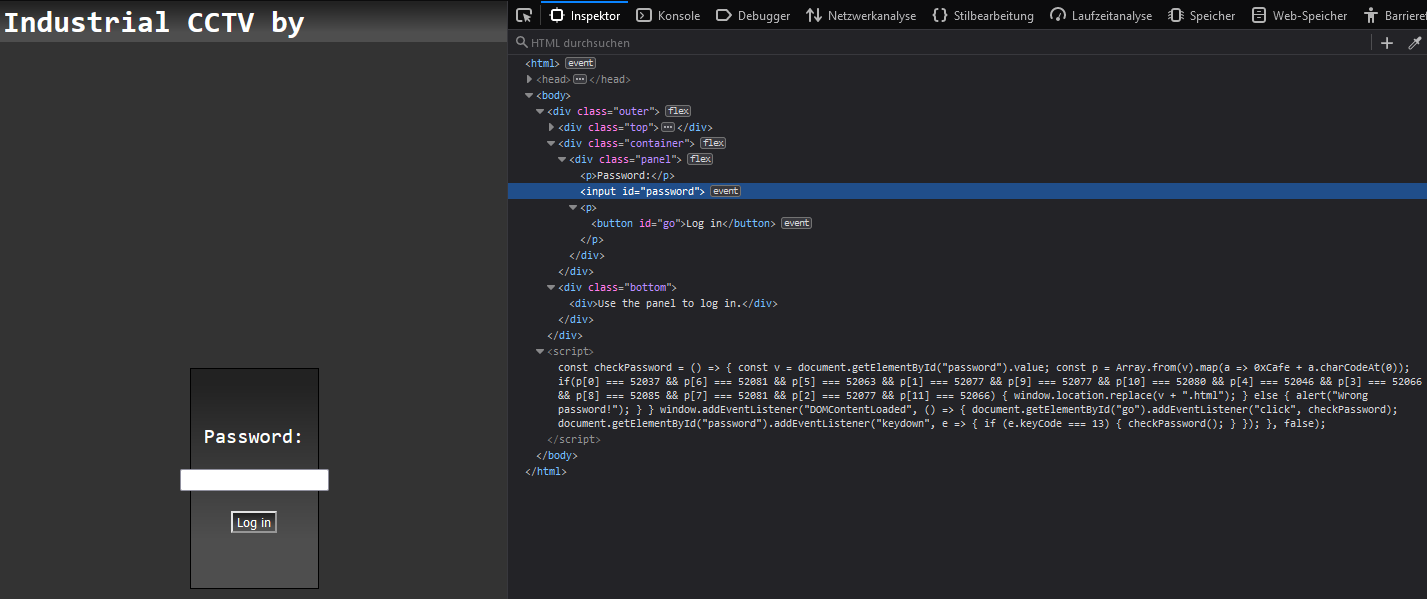
const checkPassword = () => {
const v = document.getElementById("password").value;
const p = Array.from(v).map(a => 0xCafe + a.charCodeAt(0));
if(p[0] === 52037 &&
p[6] === 52081 &&
p[5] === 52063 &&
p[1] === 52077 &&
p[9] === 52077 &&
p[10] === 52080 &&
p[4] === 52046 &&
p[3] === 52066 &&
p[8] === 52085 &&
p[7] === 52081 &&
p[2] === 52077 &&
p[11] === 52066) {
window.location.replace(v + ".html");
} else {
alert("Wrong password!");
}
}
window.addEventListener("DOMContentLoaded", () => {
document.getElementById("go").addEventListener("click", checkPassword);
document.getElementById("password").addEventListener("keydown", e => {
if (e.keyCode === 13) {
checkPassword();
}
});
}, false);
Our password is converted into an array, mapped, and compared to numbers in an if statement. 0xCafe is always 51966, so we need to find the Char Code of the letters which add up to the number sequence 52037 52077 52077 52066 52046 52063 52081 52081 52085 52077 52080 52066. The numeric difference 71 111 111 100 80 97 115 115 119 111 114 100 corresponds to the ASCII letters GoodPassword.

The flag is CTF{IJustHopeThisIsNotOnShodan}.
Prague - Apartment
Challenge: Logic Lock (misc) It turned out suspect's appartment has an electronic lock. After analyzing the PCB and looking up the chips you come to the conclusion that it's just a set of logic gates!
We are provided a file named
419bcccb21e0773e1a7db7ddcb4d557c7d19b5a76cd421851d9e20ab451702b252de11e90d14c3992f14bb4c5b330ea5368f8c52eb1e4c8f82f153aea6566d56with no file type. Running strings, we can find the filename logic-lock.png but the file does not seem to be a PNG. Instead, 7-Zip does recognize the file as a zip, which includes the mentioned PNG.
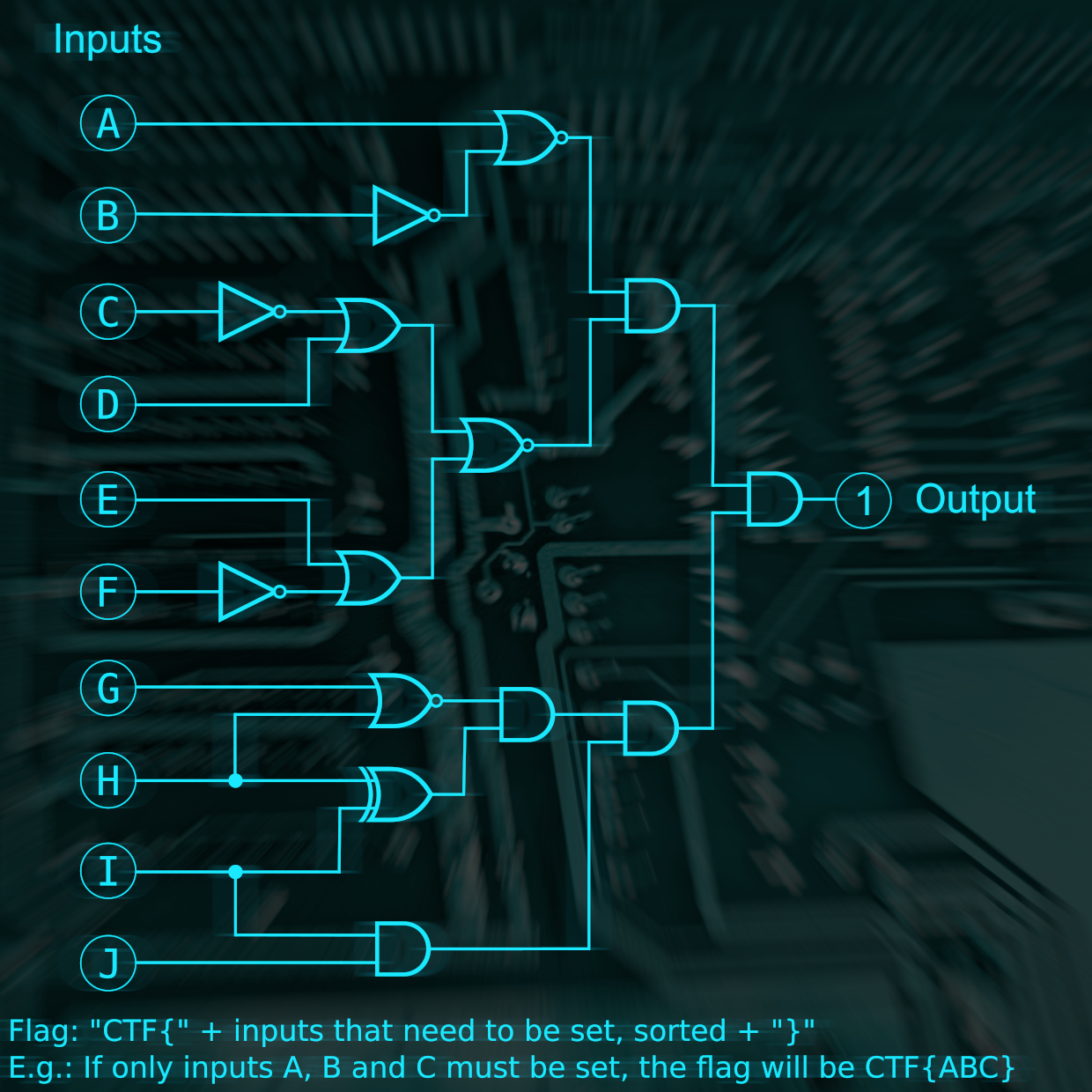
The flag is all input that has to be set in order for the output to be 1. This can be easily solved by following a logic gate diagram.
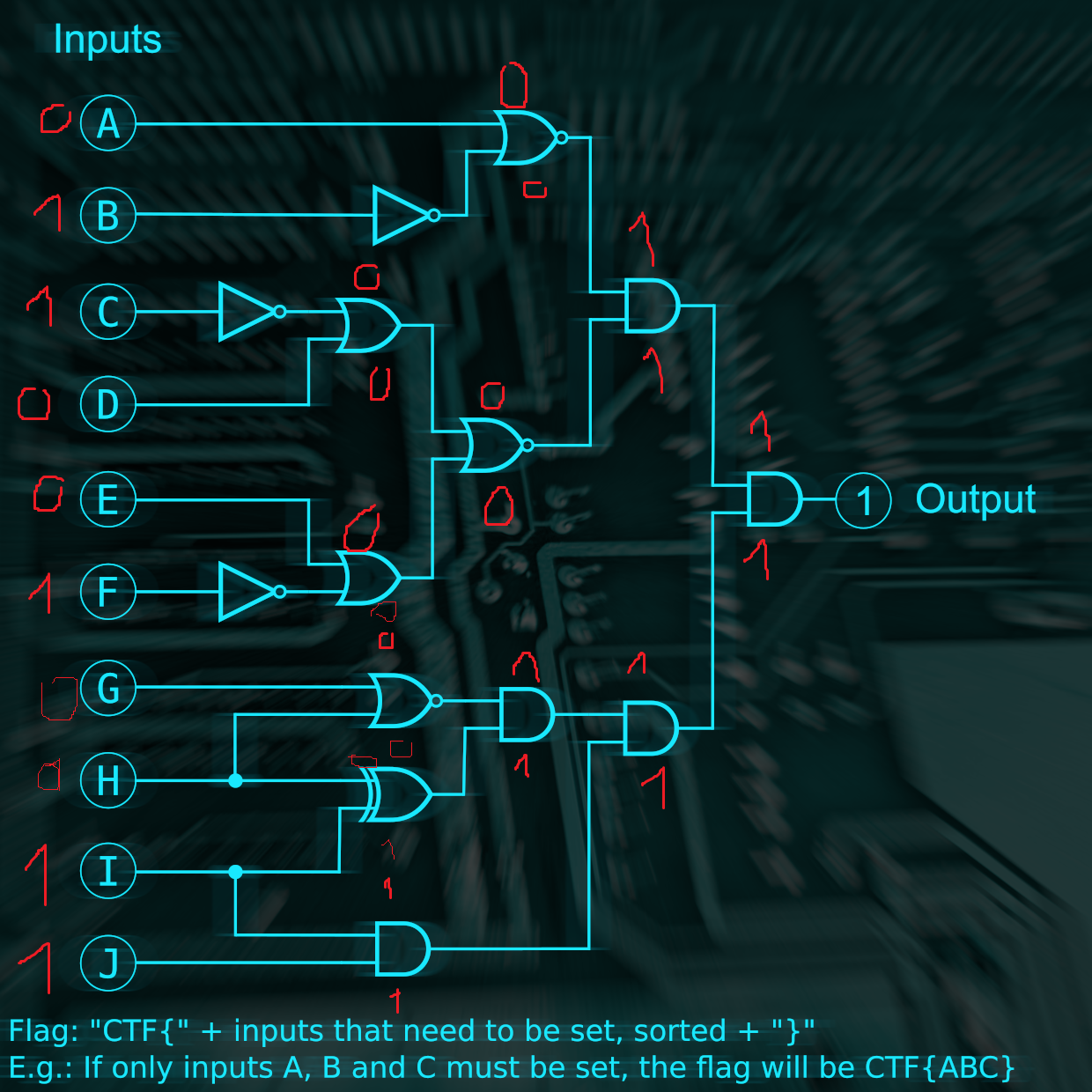
The flag is CTF{BCFIJ}.
Prague - Streets
Challenge: High Speed Chase (misc) You chase them through city streets until you reach the high way. The traffic is pretty rough for a car and you see them gaining ground - should have hotwired a motorbike as well! Too late for that. You look around your car to spot anything useful, and you notice this is actually one of the new self driving cars. You turn on the autopilot, pull out your laptop, connect it to the system, and enter the not-so-hidden developer's mode. It's time to re-program the autopilot to be a bit more useful in a chase! To make it easier, you replace the in-car LiDAR feed with a feed from an overhead sattelite - you also display it on the entertainment system. Now all that's left to do, is to write a better controlCar function!
To steer the car through the traffic, sensors are used to determine whether a vehicle is driving directly in front of us and on which side utilizing the two left and right sensors. In order not to drive against the curb and to compensate for the case of two vehicles on the side to be avoided, the embedded second if statement checks whether the value is greater than zero and one can change to this lane. Why is the value exactly 12? I have no idea; I didn`t want to put actual afford into the code, so I just tried random values until one worked.
function controlCar(scanArray)
// car to the right
if(scanArray[9] < 12 && scanArray[10] < 12){
// 2 cars or curb
if(scanArray[15] > 12 || scanArray[13] > 12){return 1}
else return -1
}
// car to the left
if(scanArray[6] < 12 && scanArray[7] < 12){
// 2 cars or curb
if(scanArray[4] > 12 || scanArray[2] > 12){return -1}
else return 1
}
return 0The flag is CTF{cbe138a2cd7bd97ab726ebd67e3b7126707f3e7f}.
Secret Location - Base
Challenge: Electronics Research Lab (hw) Welcome back AGENT. It seems like you got a lead that perhaps gives a clue about where the next journey on your quest goes. Visit the lab, and talk to Dr. Klostermann, he will know how to decrypt the device Note: If you solved the challenge before but could not submit the flag, please try again, we had the wrong flag in our database.
After unzipping the file, we get C code and a UF2 file. A UF2 file is a binary data file used by the Microsoft Programming Experience Toolkit (PXT) and MakeCode. That gives us a clue that the C code is for a microcontroller. The code uses the function gpio_clr_mask(), which drives every GPIO appearing in the mask low, and gpio_set_mask(), which drives it high. After using the functions to set the GPIO pins, we get a binary number before every sleep function, corresponding with an ASCII letter.
#include <stdbool.h>
#include "hardware/gpio.h"
#include "hardware/structs/sio.h"
#include "pico/stdlib.h"
int main(void)
{
for (int i = 0; i < 8; i++) {
gpio_init(i);
gpio_set_dir(i, GPIO_OUT);
}
gpio_put_all(0);
for (;;) {
gpio_set_mask(67); //1000011
gpio_clr_mask(0); //0000000
//1000011 --> C
sleep_us(100);
gpio_set_mask(20); //10100
gpio_clr_mask(3); //11
//1010100 --> T
sleep_us(100);
gpio_set_mask(2); //10
gpio_clr_mask(16); //10000
//1000110 --> F
sleep_us(100);
gpio_set_mask(57); //111001
gpio_clr_mask(4); //100
//1111011 --> {
sleep_us(100);
gpio_set_mask(0); //0
gpio_clr_mask(25); //11001
//1111101 --> b
sleep_us(100);
gpio_set_mask(5); //101
gpio_clr_mask(2); //10
//01100101 --> e
sleep_us(100);
gpio_set_mask(18); //10010
gpio_clr_mask(65); //1000001
// --> 6
sleep_us(100);
gpio_set_mask(1); //1
gpio_clr_mask(2); //10
// --> 5
sleep_us(100);
gpio_set_mask(64); //1000000
gpio_clr_mask(17); //10001
//01100100 --> d
sleep_us(100);
gpio_set_mask(2); //10
gpio_clr_mask(0); //0
//01100110 --> f
sleep_us(100);
gpio_set_mask(1); //1
gpio_clr_mask(6); //110
//01100001 --> a
sleep_us(100);
gpio_set_mask(18); //10010
gpio_clr_mask(65); //1000001
// --> 2
sleep_us(100);
gpio_set_mask(1); //1
gpio_clr_mask(0); //0
// --> 3
sleep_us(100);
gpio_set_mask(4); //100
gpio_clr_mask(2); //10
// --> 5
sleep_us(100);
gpio_set_mask(0); //0
gpio_clr_mask(0); //0
// --> 5
sleep_us(100);
gpio_set_mask(64); //1000000
gpio_clr_mask(16); //10000
//01100101 --> e
sleep_us(100);
gpio_set_mask(16); //10000
gpio_clr_mask(64); //1000000
// --> 5
sleep_us(100);
gpio_set_mask(2); //10
gpio_clr_mask(4); //100
// --> 3
sleep_us(100);
gpio_set_mask(0); //0
gpio_clr_mask(3); //11
// --> 0
sleep_us(100);
gpio_set_mask(9); //1001
gpio_clr_mask(0); //0
// --> 9
sleep_us(100);
gpio_set_mask(0); //0
gpio_clr_mask(1); //1
// --> 8
sleep_us(100);
gpio_set_mask(0); //0
gpio_clr_mask(8); //1000
// --> 0
sleep_us(100);
gpio_set_mask(8); //1000
gpio_clr_mask(0); //0
// --> 8
sleep_us(100);
gpio_set_mask(65); //1000001
gpio_clr_mask(24); //11000
//01100001 --> a
sleep_us(100);
gpio_set_mask(22); //10110
gpio_clr_mask(64); //1000000
// --> 7
sleep_us(100);
gpio_set_mask(0); //0
gpio_clr_mask(0); //0
// --> 7
sleep_us(100);
gpio_set_mask(0); //0
gpio_clr_mask(5); //101
// --> 2
sleep_us(100);
gpio_set_mask(0); //0
gpio_clr_mask(2); //10
// --> 0
sleep_us(100);
gpio_set_mask(65); //1000001
gpio_clr_mask(16); //10000
//01100001 --> a
sleep_us(100);
gpio_set_mask(22); //10110
gpio_clr_mask(65); //1000001
// --> 6
sleep_us(100);
gpio_set_mask(1); //1
gpio_clr_mask(6); //110
// --> 1
sleep_us(100);
gpio_set_mask(4); //100
gpio_clr_mask(0); //0
// --> 5
sleep_us(100);
gpio_set_mask(66); //1000010
gpio_clr_mask(21); //10101
//01100010 --> b
sleep_us(100);
gpio_set_mask(1); //1
gpio_clr_mask(0); //0
//01100011 --> c
sleep_us(100);
gpio_set_mask(0); //0
gpio_clr_mask(2); //10
//01100001 --> a
sleep_us(100);
gpio_set_mask(24); //11000
gpio_clr_mask(65); //1000001
// --> 8
sleep_us(100);
gpio_set_mask(67); //1000011
gpio_clr_mask(24); //11000
//01100011 --> c
sleep_us(100);
gpio_set_mask(24); //11000
gpio_clr_mask(67); //1000011
// --> 8
sleep_us(100);
gpio_set_mask(2); //10
gpio_clr_mask(8); //1000
// --> 2
sleep_us(100);
gpio_set_mask(65); //1000001
gpio_clr_mask(18); //10010
//01100001 --> a
sleep_us(100);
gpio_set_mask(16); //10000
gpio_clr_mask(64); //1000000
// --> 1
sleep_us(100);
gpio_set_mask(2); //10
gpio_clr_mask(0); //0
// --> 3
sleep_us(100);
gpio_set_mask(68); //1000100
gpio_clr_mask(19); //10011
//01100100--> d
sleep_us(100);
gpio_set_mask(19); //10011
gpio_clr_mask(64); //1000000
// --> 7
sleep_us(100);
gpio_set_mask(72); //1001000
gpio_clr_mask(2); //10
sleep_us(100);
// 01111101 --> }
gpio_set_mask(2); //10
gpio_clr_mask(117); //1110101
// 00001010 --> LF
sleep_us(100);
gpio_put_all(0);
sleep_ms(500);
}
return 0;
}
The flag is CTF{be65dfa2355e5309808a7720a615bca8c82a13d7 }.
Shenzhen - Office
Challenge: To the moon (misc) This one is a doozie. We found this weird file on a memory stick with a post-it note on it. It looks like someone was working on a very obscure encryption system. Maybe we can decode it?
Pending...